主要:
Primary Table
Constrained Table
Policy Query
Context
- ContextString: Defines a specific application context on which security policy will be enabled. It is also called an application context.
- RoleName: Defines that the security policy will only be applied to a particular Role in the application.
- RoleProperty: Used to define multiple Roles for a single security policy.
how would we set that up?
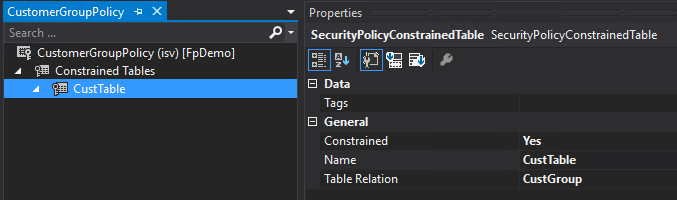
- The first thing to do is to determine your Constraint and Primary tables, in this case the CustTable table is our constraint table and the CustGroup table is our primary table.
- Next we create the policy query around our CustGroup, we want this query to return the results that we want to restrict the constraint table with
- Create a new Query, set the data source of the query to the primary table and then perform any filtering or other joins that need to be done for this query to return the results you want to filter by
- In our case we are limiting the user to only be able to see customers that have a CustGroup of ’10’ and Name of ‘Major Customers’

- Now we can create our Security Policy, we set the following parameters
- We then add a constrained table to the policy, in our case CustTable and set the following parameters
- Now if we build the solution and do a database sync of our project our XDS policy becomes live, to show what this does I did a before and after using a user assigned the FpTestRole to show the affect of the XDS policy
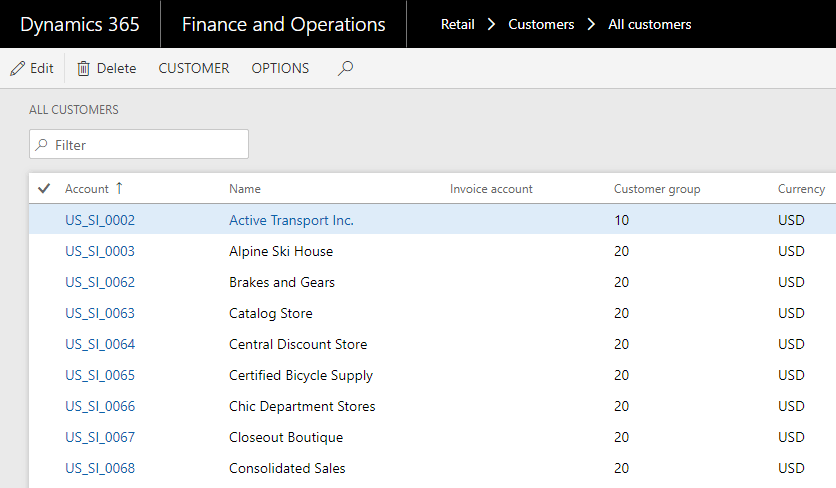
User access without XDS policy applied
User access after applying XDS policy




 留言列表
留言列表


